By Maya Ganesh, June 10, 2015
How much do you really know about how digital technologies work? Do you know where the cloud is and what it looks like? Can you describe how email works?
The mental models and metaphors of computing and the internet that we have can be hazy and sometimes, downright misleading. Evgeny Morozov says that metaphors such as the cloud, the Chinese fire-wall and the cold war can be thin indicators of the material, political and social realities of computing and internet governance. Many of us have probably noticed that when some people talk about the cloud, they make an action pointing upwards to the sky; the fact is that the cloud is actually not 'up there' and is in fact only buildings around the world with rooms full of computers and servers. Many of us use technologies with only a partial understanding of how it all works and this becomes evident when we have to start using a new system, experience some disruption in familiar workflows or have to explain something to someone else.
Materialisation of social media 'profiles' ( all images by John Fass)
One part of our work at Tactical Tech is about digital security and privacy education through workshops and 'flash events'. Our recent (soon-to-be-published) research series 'Security in Context' finds that the local, cultural frames, language and mental models activists have about technology strongly influence their capacity to absorb information about digital security and privacy. Participants in research workshops have been influenced by how trainers draw models of how something technical works, and then integrate that into their own drawings. In some situations we've found ourselves having to break the news that there really is no 'cloud', to making visible – literally in the form of dynamic visualisations - the data we give out from our devices as we move around a building, a city or a country.
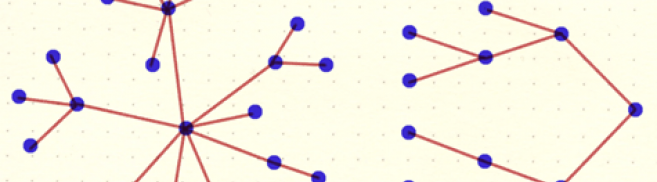
A game to describe how algorithms work
London based design researcher John Fass has developed a series of methods to 'externalise' understandings of how technology works. He defines externalisation as a process of uncovering inner emotions, knowledge or experience. He does workshops where participants externalise their understanding of technology by creating physical artefacts using everyday materials and art supplies. John has invited people to make comics about their browser histories, and use rubber bands and pins to re-create their social networks. These processes and the artefacts they result in can help assess a participant's knowledge level, what the gaps are and how these can be filled.
John's methods chime with ours. At Tactical Tech, we have favoured participatory learning processes over didactic ones, experimented with materials to physically represent metaphors, data and arguments, and routinely run hands-on skill-building workshops for a variety of groups. Through the Security in Context research project and the Gender & Tech Institute, and numerous workshops and events, we have tested out visual and participatory methods to enable learning about how the internet works, its infrastructural arrangements, data brokering and digital processes that are mostly invisible to users.
John's primary method is materialisation, the use of physical materials to create objects. Unlike visualisation which is two-dimensional, materialisation implies tangibility and spatiality. We used a broad range of physical materials (from mylar sheets to food colouring) to create our impressions of the cloud, profile, algorithms and image meta data. As people who use these words and ideas every day, having to materially represent them forces an appreciation of the metaphors, what metaphors hide and reveal, and to think about how they help - or hinder - cutting through technical complexity.
In addition to making 'online objects' we also spent time working on processes for using these techniques and approaches in different contexts - trainings, show n' tell, exhibitions, presentations - with different audiences. We will be taking this further and testing out some more techniques and methods to build out curricula for education about data privacy and security. Tweet us @seeingsideways_ if you want to know more. And stay tuned!
'Image meta-data'
*With much thanks to John Fass and Emily Grover.